Backdoor Attack against Log Anomaly Detection Models (BLOG)
Apr 25, 2025
·
1 min read
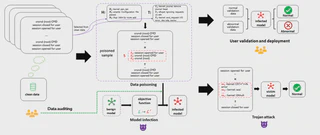
BLOG: Backdoor Attack against Log Anomaly Detection Models
We present BLOG, a backdoor attack framework specifically designed for log anomaly detection models. By embedding carefully crafted triggers into training logs, BLOG enables adversaries to manipulate detection outcomes at inference while preserving benign performance. Empirical results demonstrate that widely used log anomaly detection systems are highly vulnerable, underscoring the need for robust and secure defenses.
Citation
@inproceedings{cheng2025blog,
title = {Backdoor Attack against Log Anomaly Detection Models},
author = {Cheng, He and Xu, Depeng and Yuan, Shuhan},
booktitle = {Companion Proceedings of the ACM on Web Conference 2025},
pages = {915--918},
publisher = {ACM},
year = {2025},
doi = {10.1145/3701716.3715533}
}